Benefits at a glance
|
|

|

|
|
No administration effort One-time set-up of the SSO procedure during implementation - user ID and password are not required. |
Save time Automatic transfer of the cost centre for purchase requisitions for internal cost allocation and to support controlling. |
Efficient management Licences and favourites can be automatically assigned to specific employee groups or locations without manual assignment. |
The Nautos Single Sign-On module briefly explained:
The Nautos Single Sign-On (SSO) module offers users secure and convenient authentication with just one login process. SSO supports multi-factor authentication and ensures security by avoiding duplicate data maintenance.
SSO integration optimizes access to company applications
An SSO connection is based on the creation of a trusted connection between the application as a service provider ("SP") and a user directory service, the Identity Provider ("IdP"). This connection is similar to a "business contract" between the two parties. To secure the SSO connection, proven cryptographic methods are used that are of great importance for processes on the Internet.
SSO allows your employees to use company applications securely and provides further possibilities to centrally manage and secure this usage, and to keep an overview of all accesses.
Efficient access control
With an SSO login, an organization can centrally manage access to Nautos. The SSO procedure not only promotes an overview of the accesses of potentially authorized users to the application, but also improves the overall user experience. Thanks to the SAML2 protocol, users can also authenticate themselves to Nautos with just one centralized login process on the internal company network.
Login with SSO
For universities and research organisations, authentication with Shibboleth is possible via the DFN.
Easy implementation
Within a few hours, we can configure the SSO implementation in your system according to your specific requirements and needs. Please contact us if you want to place an order.
Alternatively, you have the option of implementing the system yourself if you have the necessary expertise. Please note, however, that no documentation is currently available.
FAQ on the Nautos SSO procedure
-
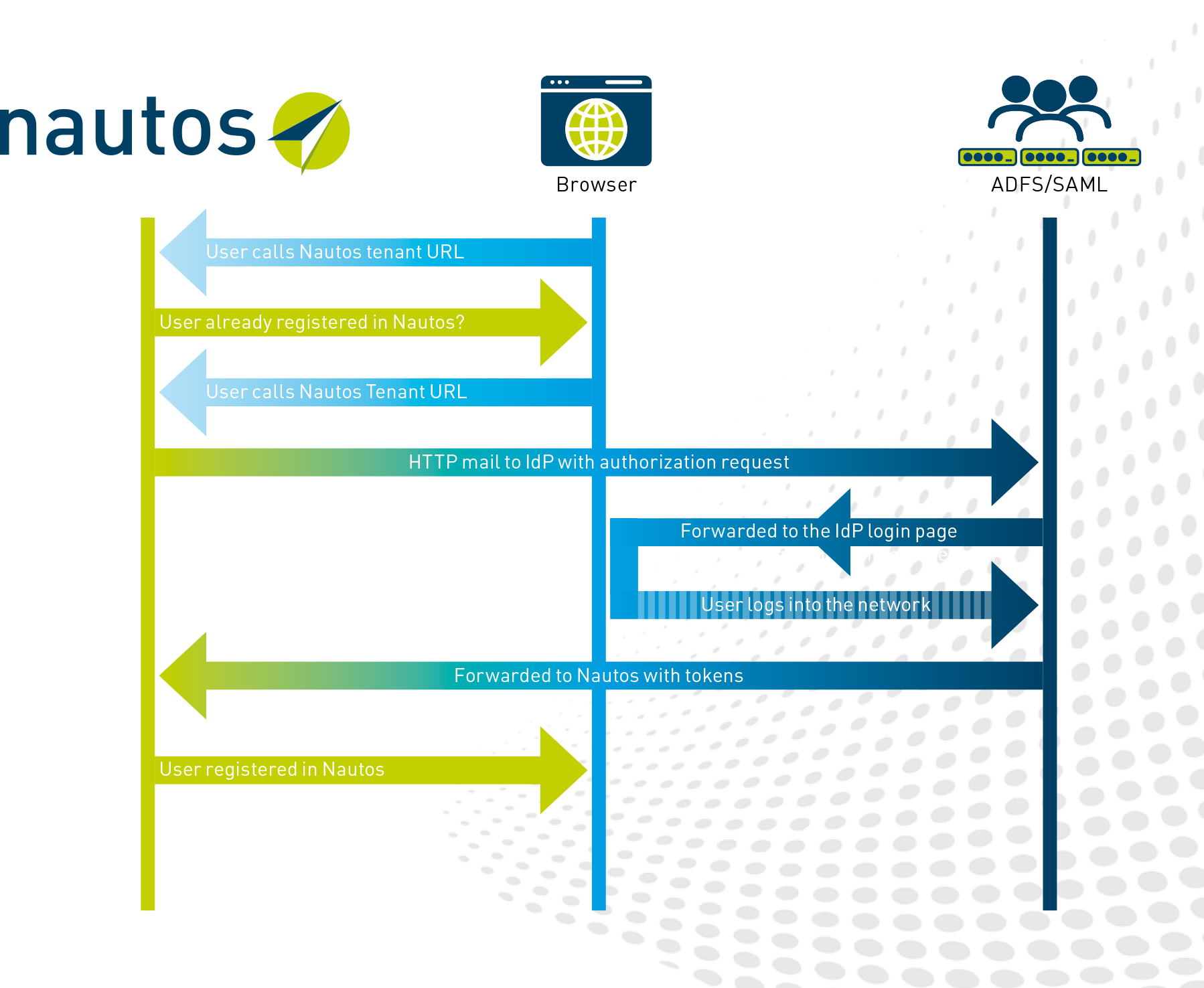
Nautos uses the SSO procedure initiated by the service provider, in which the identity provider authenticates and authorizes access to Nautos.
-
The user calls up the URL of their Nautos tenant. Nautos checks the access for authenticity and existing sessions. If required, it is forwarded to the IdP for authentication.
The IdP checks whether the user is known, authorized and logged into the network. Upon successful registration, it generates a token and transmits it to Nautos.
-
Nautos checks whether an account exists and whether all the necessary data has been provided. If necessary, a new account will be created. The user is then logged into Nautos with the assigned role.
-
Central user management offers several important advantages for your organization:
- Risk management: It ensures that only authorized internal and external services have access to organizational data and enables access rights to be checked regularly
- Centralized user data management: Redundant data maintenance is reduced, data quality is improved and effective master data management is optimized.
- Controlled user management: It provides better insight and deeper control over access and use of company-wide resources, improving the security posture and efficiency of the organization.
-
The set-up takes place in several steps:
- Publication of the basic data
- Generation and transmission of IdP metadata
- Use of metadata by Nautos.
-
Necessary attributes are:
- User name
- Site (according to the Nautos licence model)
- E-mail address
- First name
- Last name
- Role
Further optional attributes:
- Department
- Cost centre
- Title
- Initials
The attributes have specific namespaces, such as for AD FS.
-
Roles are assigned either by the IT department or by the specialist department and can be assigned to groups.
-
You can find out more about claims on the Microsoft technical reference pages for AD FS and Azure:
Discover more Nautos modules

Nautos module ReqIF converter
The latest Nautos module is an XML-based format for exchanging requirements. It enables you to use standards content in your requirements management systems in a granular way.

Nautos Online Hosting Module
Nautos now offers you a new online hosting module - the perfect cloud solution for secure access to your documents, independently of your IT, anytime and anywhere.

Nautos API Metadata Module
The API metadata module enables you to access current standards data directly from external applications and to automatically submit customer-specific search queries to Nautos.